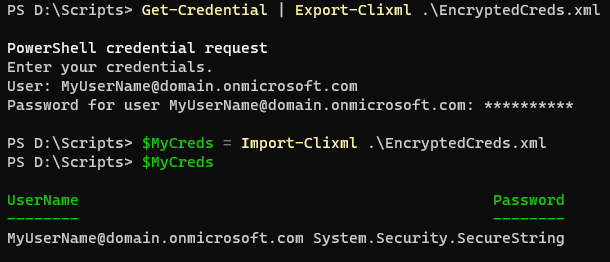
Encrypting Credentials Using a Key File
There are many ways to encrypt your credentials using PowerShell. One of the fastest/easiest ways is to export/import your credential to xml using the Export-Clixml and Import-Clixml cmdlets. This method is not very portable since the xml file can only be imported on the machine it was created it on using the same account that created it. These extra restrictions make this a somewhat secure way to encrypt your credentials but also cumbersome.
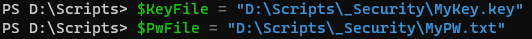
An alternative solution would be to encrypt your credentials using a key and password file which can be shared and stored on a network location to be used by any scripts across multiple servers. To do this we'll first need to create some variables to store our file paths.
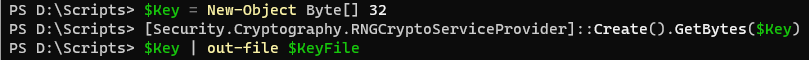
We then need to create the key that will be encrypting our password. Once created we will export it to our key file.
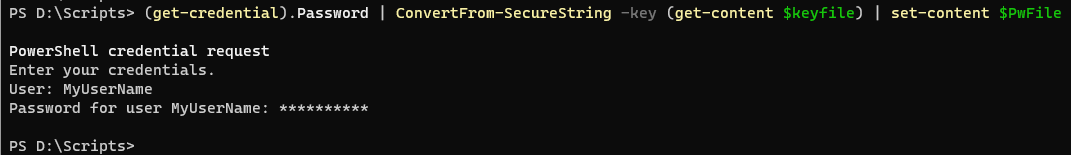
Finally, we'll use Get-Credential to capture our credential and then store it in our password file which will be encrypted with our key file.
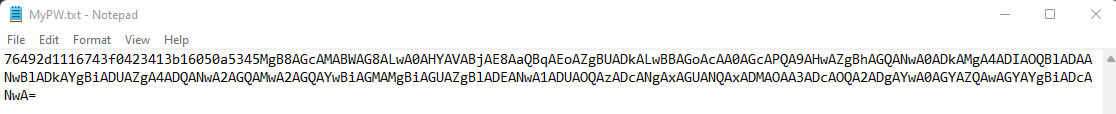
Once you have your key and password file setup, you can store them on a file share and limit access to the folder. You can also take a look at the password file to see your encrypted credential.
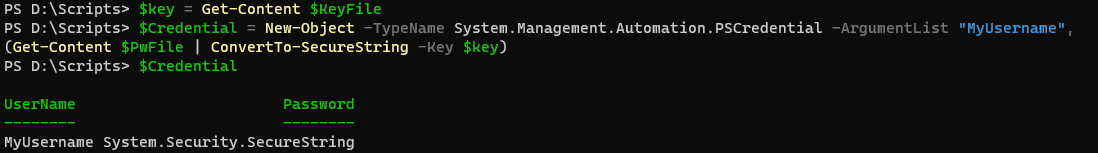
To use your credential, you will need to import your key and then create a PSCredential object using the password file and key file. The new object will have your Username and Password stored and this object can now be passed to other commands/scripts.
Unfortunately, this method is not the most secure way to store your credentials for automation. For added security be sure to use file/folder ACLs and consider storing the files separately.